Jitsi - private video conferencing server
With the recent massive shift to remote work tools like Zoom became very popular.
Zoom is not ideal for privacy nerds like me.
I decided to look for alternatives and found Jitsi. Jitsi is open source video conferencing software that you can set up on the private server (or use one of the public servers).
Fully manual setup is complicated, but luckily there is a Docker-based setup available.
Here instructions for setup on the raw CentOS 7 server:
- Setup docker & docker-compose and git:
yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
yum install -y docker-ce docker-ce-cli containerd.io screen
systemctl start docker
systemctl enable docker
yum remove -y git*
yum -y install https://centos7.iuscommunity.org/ius-release.rpm
yum -y install git2u-all
curl -L https://github.com/docker/compose/releases/download/1.25.4/docker-compose-`uname -s`-`uname -m` -o /usr/local/bin/docker-compose
chmod +x /usr/local/bin/docker-compose
- Clone the repo, create configuration folders:
git clone https://github.com/jitsi/docker-jitsi-meet && cd docker-jitsi-meet
- Setup the configuration:
cp env.example .env
vi .env
Here the list of changes I made. Enable the LetsEncrypt certificate automation, enable guests, setup the HTTP>HTTPS redirect.
# diff -u .env env.example | grep -E "^\-"
--- .env 2020-03-31 03:55:05.968349055 +0000
-HTTP_PORT=80
-HTTPS_PORT=443
-TZ=UTC
-PUBLIC_URL=https://jitsi.starikevich.com
-DOCKER_HOST_ADDRESS=134.122.88.225
-ENABLE_LETSENCRYPT=1
-LETSENCRYPT_DOMAIN=jitsi.starikevich.com
-LETSENCRYPT_EMAIL=stas[at]starikevich.com
-ENABLE_GUESTS=1
-ENABLE_HTTP_REDIRECT=1
DOCKER_HOST_ADDRESS is the real external server IP address - that’s there the WebRTC traffic get routed (UDP 10000 or TCP 4443 fallback). Setting up this option fixed my initial video problem.
- Open the following ports on the firewall or security group level (AWS). More details about ports here.
- TCP 80
- TCP 443
- TCP 4443
- UDP 10000
Docker messes up the Linux firewall (the solution is complicated but possible). I encourage you to use a hoster-provided firewall solution with docker setups (AWS - SecurityGroups, DigitalOcean - firewall).
- Open the
screenand start the containers:
screen -S jitsi
docker-compose up
The cold start will take some time (2-3 minutes) - under the hood scripts will issue the certificates, generate the Diffie-Hellman group for Forward Secrecy and configure the environment.
An important note here is that some changes in the .env file will not be reflected with the docker-compose containers starts and stops, for example, HTTP>HTTPS redirect configuration switch.
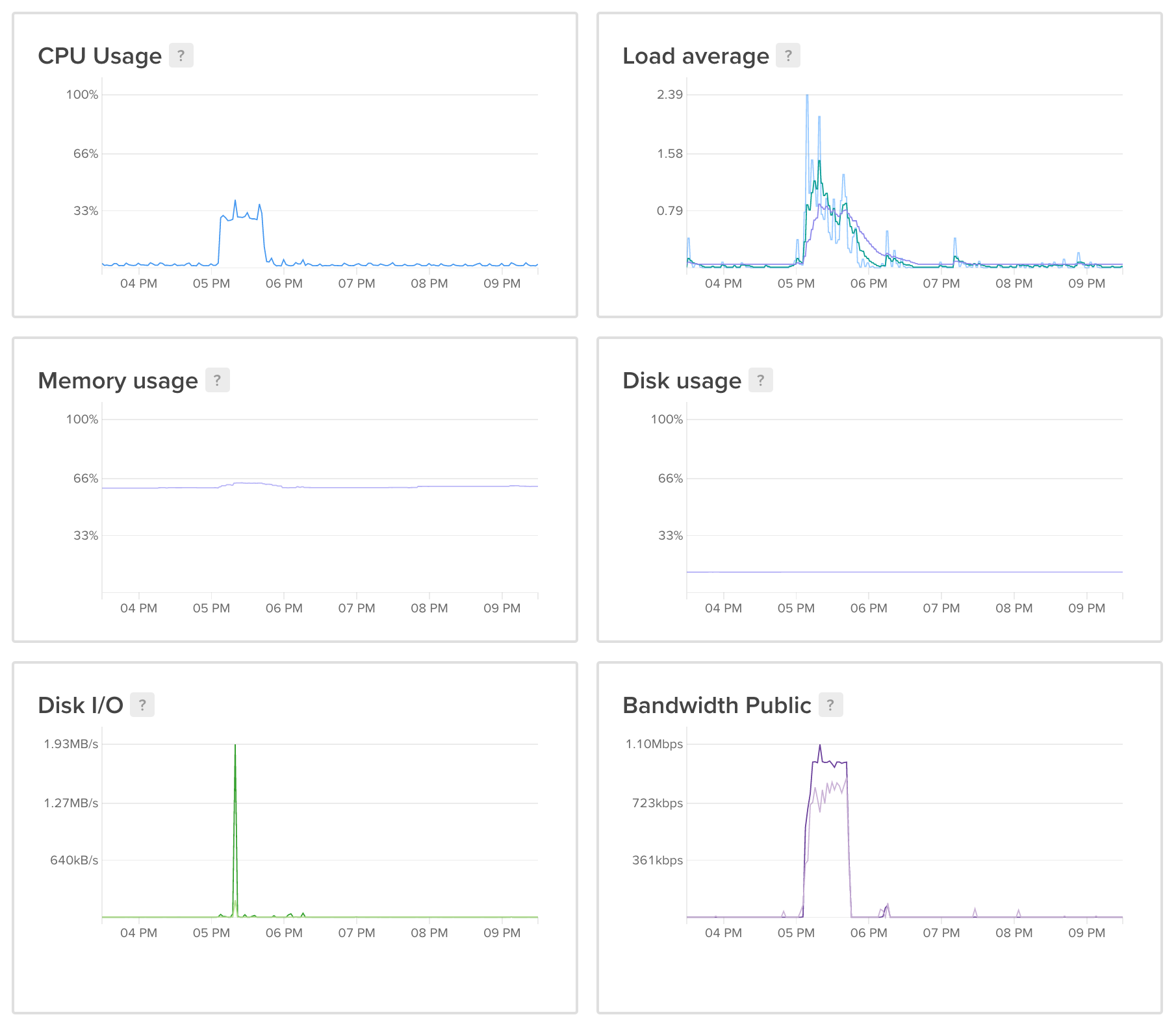
Test with 3 clients and HD-level video showed ~35% CPU usage on the entry-level ($5) droplet. No significant issues with quality or delays, everything works smoothly.
So yes, you can have a private video conferencing server with as low as $5/m.
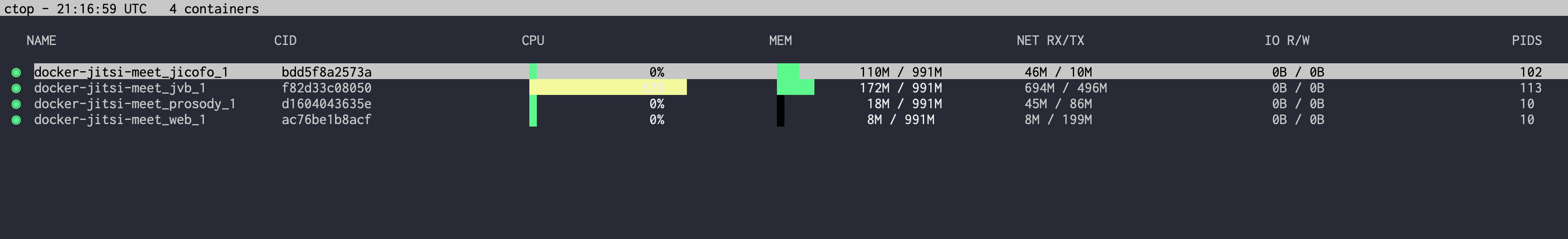
ctop output. jvb is the jitsi-videobridge container:
Few minor changes I applied to the test environment:
- Uncomment line 22 in
~/.jitsi-meet-cfg/web/nginx/nginx.confto disable emitting nginx version on error pages and in the “Server” response header field:
server_tokens off;
- Enable HTTP/2 in
~/.jitsi-meet-cfg/web/nginx/site-confs/default, line 11:
listen 443 ssl http2;
Restart the docker-jitsi-meet_web_1 to apply changes then:
docker restart docker-jitsi-meet_web_1
If everything goes well you can start the containers without screen using the -d flag (press CTRL+C in screen to stop the existing environment first):
docker-compose up -d
Useful links:
- intro into Jitsi
- Kinsing Malware Attacks Targeting Container Environments - why should have firewall in front of your Docker hosts
- Matrix and Jitsi integration - great run-through video showing installing Synapse, Riot & Jitsi on a completely fresh Debian install